Last week, I noticed new buzz word 'Cloud Logging' at our architect Ambal desk. This blog is about that.
Trust is not only a cloud issue. Alan Murphy points out that to get the benefits of clouds, one has to trust the providers for certain things, but doing so continues a trend in technology
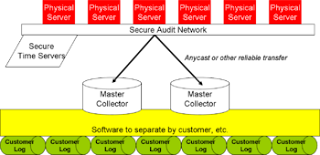
Clouds will need different audit models than do traditional data centers. The diagram shows physical servers onto which the virtual machine instances (VMI) may map. As each VMI generates a loggable event, typically using calls to syslog or snmp, the physical server inserts a time stamp from a trusted (i.e., cryptographically signed) network time protocol server, and then transmits multiple copies of the log events to distributed master logs within the provider infrastructure. At those locations, software and servers sort the log events by VMI and customer, and create viewable, secure logs that the customers can audit. This design is towards LaaS (Logging As A Service)
Alternatively, in a community cloud, independent auditors can apply suitable tests to the customer data extractors and certify them, perhaps for a given digitally signed version of the code. This design approach does assume that the VMI-hypervisor is trusted; there have been some experimental side channel attacks from one VMI to another. This is an area, especially when there are legal requirements to demonstrate due diligence, in which recognized expert help may be needed.

Interesting perspective on audit models for the cloud! I hadn’t considered how time-stamped logs from VMIs could be securely aggregated for customers. Do you think LaaS (Logging As A Service) will become a standard for compliance in cloud environments?
ReplyDelete