IIS 7 is the Web server used in Windows 7. IIS 7 has a completely modular setup design that enables control over the footprint of a Web server. IIS can be easily configured via Start->Control Panel->Programs ->Programs and Features ->Turn Windows features on or off.
Next important step is to understand the significance of each IIS option. It helps us to configure IIS for Azure development platform.
FTP Publishing Service: Installs File Transfer Protocol (FTP) Service and FTP management console. Provides support for upload and download of files.
Web Server Management Tools: Installs Web server management console and tools. It contains IIS Management Console, IIS Management scripts Tools and Management Service
Application Development Features: Installs support for application development such as ASP.NET, Classic ASP, CGI, and ISAPI extensions.
Common HTTP Features: Installs support for static Web server content such as HTML & image files, custom errors, and redirection.
Health & Diagnostics: Enables you to monitor and manage server, site, and application health such as HTTP Logging, Request Monitor, Tracing, etc.
Performance Features: Static Content Compression and Dynamic Content Compression before returning it to a client.
Security: Enables additional security protocols to secure servers, sites, applications, vdirs, and files such as Windows Authentication, Client Certificate Mapping Authentication, etc.
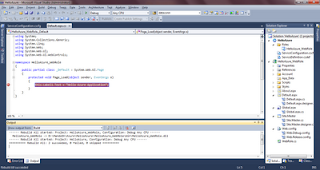
For cloud app development, I enabled Web Management Tools->IIS Management Console and all Application Development & Common HTTP Features. Apart from these, Request Filtering and Windows Authentication of Security + Static Content Compression of Performance Features. My dev box setup is attached as the snapnshot.